5 most popular browsers were tested, in alphabetical order: Apple Safari, Google Chrome, Microsoft Internet Explorer, Mozilla Firefox and Opera. Among others, the set of implemented encryption algorithms was verified, as well as efficiency of exchanging encrypted data under non-standard conditions in the network. However, the key part of the tests was the analysis of interaction between the browser and its user in cases of occurring different types of security errors embedded within browsed Web pages. For instance, an outdated certificate or unencrypted content within an HTTPS page cases were tested. It was verified whether the idiosyncrasy had been detected at all, and then – if the information about it was presented to the user in a visible, detailed and convenient way. The default settings of all browsers were assessed as well.
On the other hand, it must be clearly stated that the current stage of the tests did not concern potential vulnerabilities in the code of the browsers and any conclusions about quality in terms of software vulnerabilities must not be drawn.
It may be clearly seen that the vendors aim to create for their users conditions that would allow them to browse the Web in a secure way. However, the implementation of that goal varies between particular browsers (and sometimes is quite heterogenic within single applications). The amount of displayed information on errors that had occurred significantly varies among the browsers, which may be meaningful for particular groups of users in order to select their favorite application.
According to obtained results, no absolute leader or outsider among the tested browsers may be pointed out. In the subjective assessment of the report authors, the two most popular browsers (i.e. Firefox and Internet Explorers) fulfill the majority of basic requirements for secure handling of SSL/TLS encrypted tunnels, while Firefox appears to have better interaction with the user and slightly more secure default settings – and Internet Explorer appeared to be more efficient during sending data through encrypted tunnels.
Amongst the rest of the browsers, not so popular in the market, the report authors honored Opera for the most sophisticated error reporting facilities. It also seems that the developers of Safari still have the most work to do.
It also appears that using only one browser (not only in terms of SSL/TLS tunnels) is a solution that limits the opportunities to perceive various types of security problems – especially those users who are technically oriented.
The detailed report, summarizing the work done, may be downloaded from PSNC Security Team webpage. Currently it is available in Polish, but the authors will prepare an English, shortened version soon.
Downloads:
OSCARS: Paving the Way for Open Science in the European Research Area
2025-07-03
The European scientific landscape is undergoing a significant transformation, driven by initiatives such as OSCARS. This ambitious, four-year Horizon Europe project aims to revolutionize research practices across the continent by promoting Open Science principles and supporting the widespread adoption of FAIR (Findable, Accessible, Interoperable, Reusable) data. Our Centre has just joined OSCARS through the DARIAH-EU consortium. PCSS will focus on Work Package 2.
Poland Announces Its Participation in the EU’s AI Gigafactories Program
2025-06-12
The Polish Ministry of Digital Affairs has announced that Poland is finalizing discussions with European Union partners regarding its participation in the EU's AI Gigafactory building program. Following the conclusion of public consultations, a formal application is expected to be submitted to EU structures before 20 June 2025.
One Logo, One Name – Even More Possibilities
2025-06-02
We are pleased to announce that official name of our Center has just been unified. Henceforth, the one name that represents us globally is PCSS.
Introduction to Knowledge Graphs – The Very First GRAPHIA Webinar
2025-05-20
We are pleased to invite you to the first GRAPHIA webinar, which is going to take place on 13 June 2025 at 11:00 CEST. The online session’s title is “Introduction to Knowledge Graphs” and it will be hosted by Julien Homo.
LUMEN Is Waiting for You Online!
2025-05-20
The LUMEN (Linked User-Driven Multidisciplinary Exploration Network) project was born of cross-domain collaboration among: mathematics, social sciences and humanities (SSH), earth system and molecular dynamics. As one of the project’s partners, PSNC is proud to present LUMEN’s official website, which has recently made its online debut!
Support Cultural Heritage – Take Part in a Short 3D-4CH Survey 🙂
2025-04-30
3D-4CH is a European project the goal of which is to revolutionize the way cultural heritage is protected, digitized, and made accessible through the use of advanced 3D technologies, artificial intelligence, and extended reality. Now you can also contribute to saving the precious cultural heritage for the next generations. Just take a short survey aimed at individuals, companies, and institutions that conduct courses or workshops related to the digitization of cultural heritage. The deadline for completing this survey is 21 May 2025.
PSNC is a part of Nomios and Nokia’s Connecting Europe Tour
2025-04-24
"The Connecting Europe Tour" is a video-blog project presented by Nomios and Nokia. Nat and Fraser, two young and witty entrepreneurs are on an exciting journey across Europe to dive into the world of cutting-edge technology and innovation. Throughout the mini series the guys visit: London, Cambridge, Paris, Brussels, Amsterdam, Geneva, Berlin and Poznań – where they explore the backbone of European research and education, the GÉANT network.
PSNC Supports Cybersecurity in Business
2025-04-18
The Poznań Supercomputing and Networking Center (PCSS) and Wielkopolska Agency for Enterprise Development (WARP) signed a letter of intent regarding cooperation in the area of cybersecurity. In its initial phase, the cooperation will feature the dissemination and promotion of information about cybersecurity and the security of ICT systems among entrepreneurs in Wielkopolska (Greater Poland) Voivodeship.
Fifth Edition of the European Quantum Systems and Software Summit at PCSS
2025-06-27
Following a successful series of European Quantum Systems and Software Summits (EQS3) over the past three years, the fifth edition of this event was held in Poznań. This year's three-day meeting (25-27 June) was co-organized by a renowned quantum expert dr. hab. inż. Krzysztof Kurowski with the support of the Poznań Supercomputing and Networking Center (PCSS). EQS3 is a closed conference, aimed at the European scientific community and its international partners, with the primary goal of further shaping a common vision and strategy for the development of European quantum and hybrid systems.
PCSS Is a Partner of the “Quantum Babylon” Exhibition
2025-06-27
We are thrilled to announce our institutional partnership with the "Quantum Babylon" exhibition, currently on display at the National Museum in Szczecin. The vernissage, held on 26 June 2025, drew not only contemporary art enthusiasts and admirers of Roman Lipski's work, but also an international group of experimentalists who harness modern technologies to create new dimensions in art & science.
Innovative Space Research: Inauguration of the LOFAR ERIC Project at PCSS
2025-06-26
On 25 June 2025, PCSS hosted a special meeting of POLFAR, combined with the opening of the LOFAR ERIC European Research Infrastructure Consortium's operations in Poland. Among the guests were representatives from the Ministry of Science and Higher Education, the Space Research Centre of the Polish Academy of Sciences, the SOLARIS National Synchrotron Radiation Centre, ESO, CTAO ERIC, and, of course, members of the POLFAR consortium, including PCSS.
The Launch of the First Polish AI Factory – PIAST-AI
2025-06-23
Today at PCSS a significant step towards making Europe a leader in AI technology has been taken. The PIAST-AI Factory at the Poznań Center was selected by the European Commission to participate in the "AI Factories" program. This makes the Capital of Wielkopolska region a crucial driving force in the development of fields such as: IT, cybersecurity, space technologies, robotics, and sustainable development.
Inauguration of PIAST-Q – A Leap for European Quantum Computing
2025-06-23
Today, under the Polish Presidency of the Council of the European Union, EuroHPC JU inaugurated PIAST-Q in Poznań (Poland). This first inauguration of a EuroHPC quantum computer marks a milestone in building a European quantum computing infrastructure. This is also the first EuroHPC infrastructure located in Poland.
DARIAH Annual Event 2025: The Future of Digital Humanities in Göttingen
2025-06-21
From 17 to 20 June 2025, the prestigious DARIAH Annual Event 2025 took place in Göttingen (Germany). The Göttingen State and University Library was chosen as the venue for this event, gathering experts and enthusiasts of digital humanities from all over Europe, including representatives of PCSS. The first day was dedicated to internal DARIAH meetings, while the main part of the conference ran from 18 to 20 June.
Digital Summit in Gdańsk
2025-06-19
On 17 and 18 June 2025, the Digital Summit conference was held at the European Solidarity Centre in Gdańsk. This event created a space for discussion on Europe's digital future, involving ministers, technology industry leaders, scientists, and representatives of the most innovative companies; Robert Pękal, the Director of PCSS, was among them. During the conference, Poland's presidency of the EU Council in the area of digitalization was summarized, and common plans for this area of activity for the coming years were outlined.
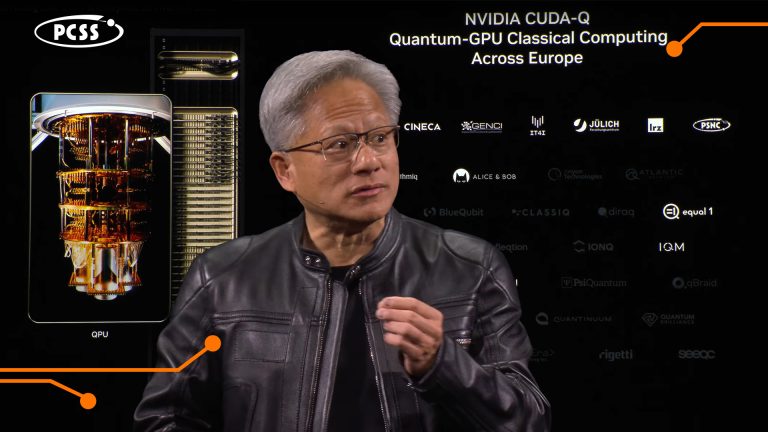
PCSS Quantum Technologies at NVIDIA GTC in Paris
2025-06-17
At the NVIDIA GTC AI conference for developers in Paris (10-12 June 2025), the PCSS’ name appeared among the leading European institutions in the realm of quantum computing during the speech of the NVIDIA co-founder and CEO, Jensen Huang.
About PSNC in GÉANT CONNECT
2025-06-10
The latest, June issue of the magazine "CONNECT", focused on the GÉANT network and community, features an article on next-generation research infrastructures. These projects are being implemented within four leading projects run by PCSS and based on the PIONIER Network.
“Long-Distance Coherent Quantum Communications in Deployed Telcom Networks” – Piotr Rydlichowski in Nature Magazine
2025-04-24
The newest issue of Nature magazine (04/2025) features an article titled “Long-Distance Coherent Quantum Communications in Deployed Telcom Networks” and one of its coauthors is Piotr Rydlichowski – a PSNC’s researcher from the Centre’s Network Technologies Division.
GÉANT’s “Foresight 2030: Navigating Change” Report
2025-01-08
At the end of 2024, GÉANT released a report identifying the key opportunities and challenges facing the NREN community (National Research and Education Network) in the coming decade. One of the authors of this document is Raimundas Tuminauskas – Head of the Network Infrastructure and Services Department at PSNC.
Nobel Prizes 2024: AI in Physics and Chemistry
2024-10-17
This year's Nobel Prizes in Physics and Chemistry highlight the groundbreaking role of artificial intelligence in those fields. To get insights into this significant development, we reached out to Dr Mikołaj Buchwald – an expert from the PSNC Internet Services Department, whose research interests include cognitive neuroscience, machine learning methodology, as well as using AI plus advanced data analysis to explain human physiology and psychology.
PSNC Leaps into the future of computing
2024-09-04
Thanks to the Dariah.lab infrastructure, the first pilot projects for the preservation and dissemination of cultural heritage resources have been implemented in 2023. Dariah.lab is a research infrastructure for the humanities and arts, built as part of the DARIAH-PL project. It serves to acquire, store and integrate cultural data from the humanities and social sciences, and to process, visualise and share digital resources.
International Media on PSNC
2024-09-03
Here is a short sellection of recent articles on PSNC that have appeared in some international media.
Dariah.lab: cultural heritage documentation
2024-04-19
Thanks to the Dariah.lab infrastructure, the first pilot projects for the preservation and dissemination of cultural heritage resources have been implemented in 2023. Dariah.lab is a research infrastructure for the humanities and arts, built as part of the DARIAH-PL project. It serves to acquire, store and integrate cultural data from the humanities and social sciences, and to process, visualise and share digital resources.
Experiments using the largest IBM Q quantum computers
2024-04-14
The Polish Quantum Computing Node established at the Poznań Supercomputing and Networking Center - IBM Quantum Innovation Center - focused its activities in 2023 on expanding partnerships with leading centers and teams dealing with the development of quantum algorithms and their potential applications.
OSCARS: Paving the Way for Open Science in the European Research Area
2025-07-03
The European scientific landscape is undergoing a significant transformation, driven by initiatives such as OSCARS. This ambitious, four-year Horizon Europe project aims to revolutionize research practices across the continent by promoting Open Science principles and supporting the widespread adoption of FAIR (Findable, Accessible, Interoperable, Reusable) data. Our Centre has just joined OSCARS through the DARIAH-EU consortium. PCSS will focus on Work Package 2.
Fifth Edition of the European Quantum Systems and Software Summit at PCSS
2025-06-27
Following a successful series of European Quantum Systems and Software Summits (EQS3) over the past three years, the fifth edition of this event was held in Poznań. This year's three-day meeting (25-27 June) was co-organized by a renowned quantum expert dr. hab. inż. Krzysztof Kurowski with the support of the Poznań Supercomputing and Networking Center (PCSS). EQS3 is a closed conference, aimed at the European scientific community and its international partners, with the primary goal of further shaping a common vision and strategy for the development of European quantum and hybrid systems.
About PSNC in GÉANT CONNECT
2025-06-10
The latest, June issue of the magazine "CONNECT", focused on the GÉANT network and community, features an article on next-generation research infrastructures. These projects are being implemented within four leading projects run by PCSS and based on the PIONIER Network.
Poland Announces Its Participation in the EU’s AI Gigafactories Program
2025-06-12
The Polish Ministry of Digital Affairs has announced that Poland is finalizing discussions with European Union partners regarding its participation in the EU's AI Gigafactory building program. Following the conclusion of public consultations, a formal application is expected to be submitted to EU structures before 20 June 2025.
PCSS Is a Partner of the “Quantum Babylon” Exhibition
2025-06-27
We are thrilled to announce our institutional partnership with the "Quantum Babylon" exhibition, currently on display at the National Museum in Szczecin. The vernissage, held on 26 June 2025, drew not only contemporary art enthusiasts and admirers of Roman Lipski's work, but also an international group of experimentalists who harness modern technologies to create new dimensions in art & science.
“Long-Distance Coherent Quantum Communications in Deployed Telcom Networks” – Piotr Rydlichowski in Nature Magazine
2025-04-24
The newest issue of Nature magazine (04/2025) features an article titled “Long-Distance Coherent Quantum Communications in Deployed Telcom Networks” and one of its coauthors is Piotr Rydlichowski – a PSNC’s researcher from the Centre’s Network Technologies Division.
One Logo, One Name – Even More Possibilities
2025-06-02
We are pleased to announce that official name of our Center has just been unified. Henceforth, the one name that represents us globally is PCSS.
Innovative Space Research: Inauguration of the LOFAR ERIC Project at PCSS
2025-06-26
On 25 June 2025, PCSS hosted a special meeting of POLFAR, combined with the opening of the LOFAR ERIC European Research Infrastructure Consortium's operations in Poland. Among the guests were representatives from the Ministry of Science and Higher Education, the Space Research Centre of the Polish Academy of Sciences, the SOLARIS National Synchrotron Radiation Centre, ESO, CTAO ERIC, and, of course, members of the POLFAR consortium, including PCSS.
GÉANT’s “Foresight 2030: Navigating Change” Report
2025-01-08
At the end of 2024, GÉANT released a report identifying the key opportunities and challenges facing the NREN community (National Research and Education Network) in the coming decade. One of the authors of this document is Raimundas Tuminauskas – Head of the Network Infrastructure and Services Department at PSNC.
Introduction to Knowledge Graphs – The Very First GRAPHIA Webinar
2025-05-20
We are pleased to invite you to the first GRAPHIA webinar, which is going to take place on 13 June 2025 at 11:00 CEST. The online session’s title is “Introduction to Knowledge Graphs” and it will be hosted by Julien Homo.
The Launch of the First Polish AI Factory – PIAST-AI
2025-06-23
Today at PCSS a significant step towards making Europe a leader in AI technology has been taken. The PIAST-AI Factory at the Poznań Center was selected by the European Commission to participate in the "AI Factories" program. This makes the Capital of Wielkopolska region a crucial driving force in the development of fields such as: IT, cybersecurity, space technologies, robotics, and sustainable development.
Nobel Prizes 2024: AI in Physics and Chemistry
2024-10-17
This year's Nobel Prizes in Physics and Chemistry highlight the groundbreaking role of artificial intelligence in those fields. To get insights into this significant development, we reached out to Dr Mikołaj Buchwald – an expert from the PSNC Internet Services Department, whose research interests include cognitive neuroscience, machine learning methodology, as well as using AI plus advanced data analysis to explain human physiology and psychology.
LUMEN Is Waiting for You Online!
2025-05-20
The LUMEN (Linked User-Driven Multidisciplinary Exploration Network) project was born of cross-domain collaboration among: mathematics, social sciences and humanities (SSH), earth system and molecular dynamics. As one of the project’s partners, PSNC is proud to present LUMEN’s official website, which has recently made its online debut!
Inauguration of PIAST-Q – A Leap for European Quantum Computing
2025-06-23
Today, under the Polish Presidency of the Council of the European Union, EuroHPC JU inaugurated PIAST-Q in Poznań (Poland). This first inauguration of a EuroHPC quantum computer marks a milestone in building a European quantum computing infrastructure. This is also the first EuroHPC infrastructure located in Poland.
PSNC Leaps into the future of computing
2024-09-04
Thanks to the Dariah.lab infrastructure, the first pilot projects for the preservation and dissemination of cultural heritage resources have been implemented in 2023. Dariah.lab is a research infrastructure for the humanities and arts, built as part of the DARIAH-PL project. It serves to acquire, store and integrate cultural data from the humanities and social sciences, and to process, visualise and share digital resources.
Support Cultural Heritage – Take Part in a Short 3D-4CH Survey 🙂
2025-04-30
3D-4CH is a European project the goal of which is to revolutionize the way cultural heritage is protected, digitized, and made accessible through the use of advanced 3D technologies, artificial intelligence, and extended reality. Now you can also contribute to saving the precious cultural heritage for the next generations. Just take a short survey aimed at individuals, companies, and institutions that conduct courses or workshops related to the digitization of cultural heritage. The deadline for completing this survey is 21 May 2025.
DARIAH Annual Event 2025: The Future of Digital Humanities in Göttingen
2025-06-21
From 17 to 20 June 2025, the prestigious DARIAH Annual Event 2025 took place in Göttingen (Germany). The Göttingen State and University Library was chosen as the venue for this event, gathering experts and enthusiasts of digital humanities from all over Europe, including representatives of PCSS. The first day was dedicated to internal DARIAH meetings, while the main part of the conference ran from 18 to 20 June.
International Media on PSNC
2024-09-03
Here is a short sellection of recent articles on PSNC that have appeared in some international media.
PSNC is a part of Nomios and Nokia’s Connecting Europe Tour
2025-04-24
"The Connecting Europe Tour" is a video-blog project presented by Nomios and Nokia. Nat and Fraser, two young and witty entrepreneurs are on an exciting journey across Europe to dive into the world of cutting-edge technology and innovation. Throughout the mini series the guys visit: London, Cambridge, Paris, Brussels, Amsterdam, Geneva, Berlin and Poznań – where they explore the backbone of European research and education, the GÉANT network.
Digital Summit in Gdańsk
2025-06-19
On 17 and 18 June 2025, the Digital Summit conference was held at the European Solidarity Centre in Gdańsk. This event created a space for discussion on Europe's digital future, involving ministers, technology industry leaders, scientists, and representatives of the most innovative companies; Robert Pękal, the Director of PCSS, was among them. During the conference, Poland's presidency of the EU Council in the area of digitalization was summarized, and common plans for this area of activity for the coming years were outlined.
Dariah.lab: cultural heritage documentation
2024-04-19
Thanks to the Dariah.lab infrastructure, the first pilot projects for the preservation and dissemination of cultural heritage resources have been implemented in 2023. Dariah.lab is a research infrastructure for the humanities and arts, built as part of the DARIAH-PL project. It serves to acquire, store and integrate cultural data from the humanities and social sciences, and to process, visualise and share digital resources.
PSNC Supports Cybersecurity in Business
2025-04-18
The Poznań Supercomputing and Networking Center (PCSS) and Wielkopolska Agency for Enterprise Development (WARP) signed a letter of intent regarding cooperation in the area of cybersecurity. In its initial phase, the cooperation will feature the dissemination and promotion of information about cybersecurity and the security of ICT systems among entrepreneurs in Wielkopolska (Greater Poland) Voivodeship.
PCSS Quantum Technologies at NVIDIA GTC in Paris
2025-06-17
At the NVIDIA GTC AI conference for developers in Paris (10-12 June 2025), the PCSS’ name appeared among the leading European institutions in the realm of quantum computing during the speech of the NVIDIA co-founder and CEO, Jensen Huang.
Experiments using the largest IBM Q quantum computers
2024-04-14
The Polish Quantum Computing Node established at the Poznań Supercomputing and Networking Center - IBM Quantum Innovation Center - focused its activities in 2023 on expanding partnerships with leading centers and teams dealing with the development of quantum algorithms and their potential applications.




![The image displays the word "LUMEN" in a stylized, outlined font, with different letters connected by lines and arrows to various academic disciplines. The letters "L" and "U" on the left are linked to "Mathematics [Maths]" and "Social Sciences and Humanities [SSH]," while the letters "M," "E," and "N" on the right are associated with "Earth System Science [ESS]" and "Molecular Dynamics [MD]." The overall design suggests an interconnectedness of these fields, potentially illustrating the interdisciplinary nature of something represented by "LUMEN".](https://www.psnc.pl/files/2025/05/lumen2_EN-768x432.jpg)